In today’s hyper-connected digital landscape, ensuring robust network security has become paramount for organisations across all industries. As cyber-threats continue to evolve and grow in sophistication, companies must deploy comprehensive security solutions that protect their sensitive data, intellectual property, and customer information. Cisco Identity Services Engine (ISE) is a powerful network access control system that offers numerous advantages for organisations seeking to fortify their security infrastructure. In this blog post, we will explore the benefits of ISE and shed light on why conducting a proof of concept (PoC) is crucial before implementation.
Advantages of Cisco ISE:
- Enhanced Network Visibility and Control:
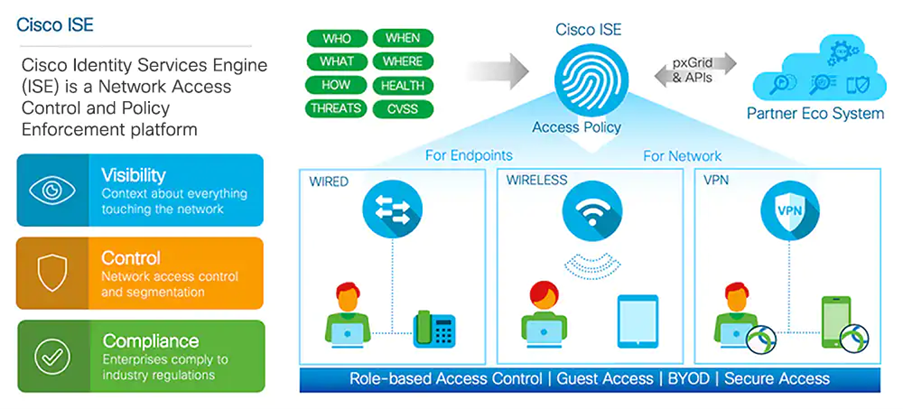
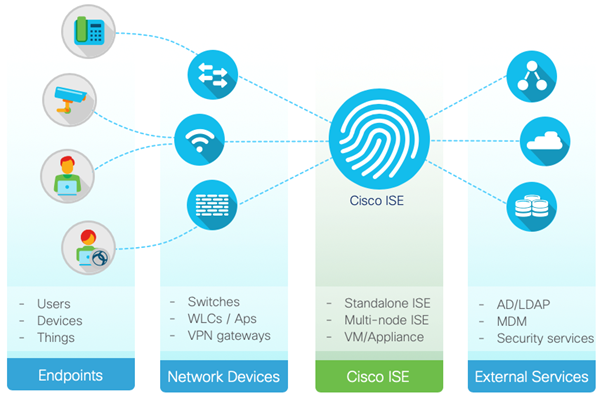
ISE provides real-time visibility into network traffic, devices, and users, enabling organisations to identify and authenticate all connected endpoints. By gaining granular insights into who is accessing the network, what devices they are using, and their level of authorisation, companies can enforce access policies and controls more effectively. This enhanced visibility empowers IT teams to identify and respond to potential security threats promptly, reducing the risk of unauthorised access or data breaches.
- Simplified Access Management:
ISE simplifies the management of user access across the network. It offers centralised control and policy enforcement, allowing organisations to define access policies based on user roles, device types, and location. This streamlined approach ensures consistent security measures across the entire network infrastructure, irrespective of the access method or device used. Administrators can easily configure policies, authenticate users, and dynamically apply access rules, reducing the administrative burden and minimising the chances of misconfigurations.
- Integration with Existing Infrastructure:
One of the key strengths of ISE is its ability to seamlessly integrate with other security solutions and network infrastructure. It supports a wide range of industry-standard protocols, enabling organisations to leverage their existing investments in authentication methods such as Active Directory, Lightweight Directory Access Protocol (LDAP), and Remote Authentication Dial-In User Service (RADIUS). This integration simplifies deployment and enhances interoperability, ensuring a cohesive security ecosystem that works in harmony with existing infrastructure components.
- Improved Compliance and Regulatory Adherence:
Meeting regulatory requirements and maintaining compliance with industry standards is a critical aspect of network security. ISE offers built-in frameworks and templates that help organisations comply with various regulations, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). By enforcing access policies, monitoring network activities, and generating comprehensive audit reports, ISE enables organisations to demonstrate compliance and minimise the risk of penalties and legal consequences.
Importance of a Proof of Concept:
A proof of concept (PoC) serves as a vital step before implementing ISE within an organisation’s network infrastructure. Here’s why a PoC is crucial:
- Evaluation of Compatibility:
Conducting a PoC allows organisations to assess the compatibility of ISE with their existing network infrastructure, applications, and security systems. It provides an opportunity to identify any potential integration challenges or conflicts, ensuring a smooth implementation process. Additionally, a PoC enables organisations to evaluate the scalability and performance of ISE in their specific environment, making informed decisions about deployment.
- Customisation and Tailoring:
Every organisation has unique security requirements and operational workflows. A PoC enables organisations to customise ISE according to their specific needs and validate its efficacy in addressing their security challenges. By testing different configurations, policies, and use cases, organisations can fine-tune ISE to align with their security objectives and maximise its effectiveness.
- Stakeholder Buy-in:
Implementing a network access control system like ISE impacts multiple stakeholders within an organisation. Conducting a PoC provides an opportunity to involve key stakeholders, such as IT administrators, security teams, and business leaders, in the decision-making process. Demonstrating the benefits and value of Cisco ISE through a PoC helps gain buy-in from stakeholders, fostering a smoother adoption and implementation process.
ISE offers a comprehensive network access control solution that enhances network security, simplifies access management, and ensures regulatory compliance. However, before implementing Cisco ISE, conducting a proof of concept is essential to evaluate compatibility, customise the solution, and gain stakeholder buy-in. By leveraging the advantages of ISE and conducting a PoC, organisations can strengthen their network security posture and protect their valuable assets in today’s evolving threat landscape.
Looking into your organisation’s security posture? We can assist with a review of your existing infrastructure and processes here.




