In today’s rapidly evolving digital landscape, ensuring robust cyber-security measures is paramount for organisations of all sizes. With the rise of sophisticated cyber-threats, traditional security models that rely on perimeter defences alone are no longer sufficient. This is where the concept of Zero Trust steps in to revolutionise the way we approach cyber-security. In this blog post, we will delve into the significance of Zero Trust and explain why Cisco should be a top contender in your organisation’s considerations for implementing this approach.
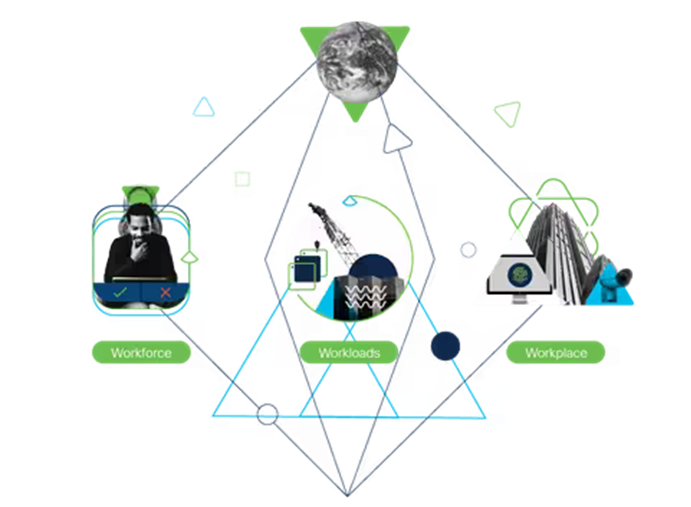
Understanding Zero Trust
The Need for Zero Trust:
- Traditional security models and their limitations.
- The increasing complexity of cyber-threats.
- The rise of cloud computing, remote work, and BYOD (Bring Your Own Device) practices.
Introducing Zero Trust:
- Core principles and foundations of Zero Trust
- The shift from network-centric to user-centric security.
- The importance of continuous authentication and authorisation.
Advantages of Zero Trust
Enhanced Security:
- The elimination of implicit trust.
- Minimising the attack surface by implementing strict access controls.
- Improved visibility and control over network activities.
Adaptability to Modern IT Environments:
- Enabling secure access for remote employees and third-party vendors.
- Supporting cloud-based applications and distributed networks.
- Facilitating secure mobility and IoT (Internet of Things) integration.
Defence-in-Depth Approach:
- Layered security measures to protect critical assets.
- Micro-segmentation and granular access controls.
- Preventing lateral movement and containing potential breaches.
Cisco: A Leading Contender in Zero Trust
Cisco’s Zero Trust Approach:
- Cisco’s extensive experience and expertise in cyber-security.
- Comprehensive portfolio of Zero Trust solutions.
- A holistic approach to Zero Trust, encompassing network, endpoint, and cloud security.
Key Features and Benefits of Cisco’s Zero Trust Solutions:
- Secure access with Cisco Secure Network Access Control.
- Endpoint security with Cisco SecureX.
- Cloud security with Cisco Secure Cloud Analytics.
Integration and Scalability:
- Seamless integration with existing Cisco infrastructure.
- Scalable solutions to accommodate evolving organisational needs.
- Centralised management and unified visibility across the network.
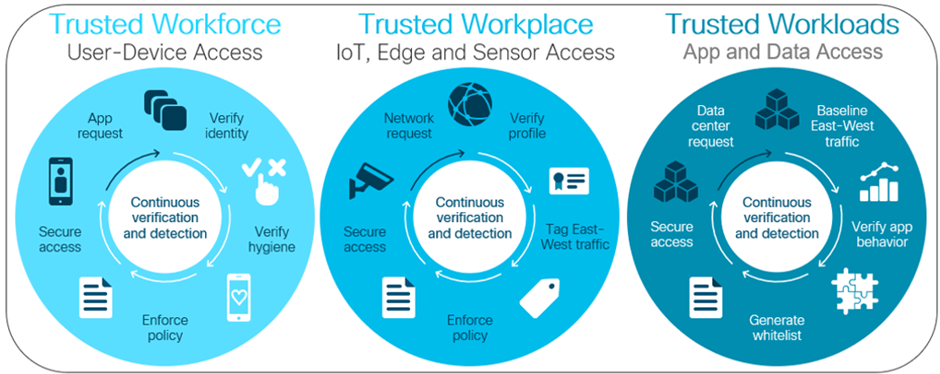
In the face of sophisticated cyber threats, organisations must embrace the Zero Trust model to protect their digital assets effectively. By adopting a user-centric approach and implementing robust access controls, organisations can establish a strong cyber-security posture. Cisco, with its vast experience and comprehensive portfolio of Zero Trust solutions, stands out as a key contender in the realm of cyber-security. Its ability to provide end-to-end security, seamless integration, and scalability makes it an ideal choice for organisations looking to strengthen their defences and ensure a secure digital environment.
Remember, the journey towards Zero Trust will require careful planning and collaboration with experienced cyber-security professionals. By partnering with Cisco and Re-solution, you can confidently embark on this transformation, knowing that you have a trusted ally to guide you through the complexities of securing your organisation in the modern digital age.
Reach out to us for an initial chat surrounding your journey to Zero-Trust.




