
Data encryption is a vital measure for securing sensitive information in our digitised world. It transforms readable data into an unreadable format, shielding valuable assets from potential cyber threats. Shockingly, research indicates that seven million unencrypted data records are compromised every day, highlighting the urgency for organisations to adopt effective protective strategies. But here’s the twist: many still underestimate the importance of data encryption, viewing it as a mere technicality rather than a critical defence mechanism. Embracing robust encryption solutions not only protects data but also builds trust with customers, ensuring their peace of mind.
Table of Contents
- Understanding Data Encryption Methods
- Why Data Encryption Is Crucial
- Practical Data Encryption Applications
- Implementing Effective Encryption Strategies
Quick Summary
| Takeaway | Explanation |
|---|---|
| Symmetric vs Asymmetric Encryption | Understanding the difference between symmetric (uses a single key) and asymmetric (uses a public and a private key) encryption methods is crucial for organisations to choose the appropriate data protection strategy. |
| Importance of Encryption in Regulation | Organisations face severe penalties for non-compliance with data protection regulations like GDPR, highlighting the necessity of robust encryption to mitigate legal risks. |
| Financial and Reputational Risks | Data breaches can result in significant financial losses and reputational damage, making encryption an essential defence mechanism to protect sensitive information and maintain customer trust. |
| Multi-Dimensional Protection Approach | Implementing a comprehensive security framework that includes data encryption at rest, in transit, and during processing significantly enhances an organisation’s overall data security posture. |
| Future-Proofing Against Quantum Threats | As quantum computing emerges, organisations must adopt post-quantum cryptography to protect against advanced computational threats, ensuring long-term data security in an evolving landscape. |
Understanding Data Encryption Methods
Data encryption is a critical security mechanism that transforms sensitive information into an unreadable format, protecting digital assets from unauthorised access and potential cyber threats. By converting readable data into a coded format, organisations can safeguard their most valuable digital resources across various technological platforms.
Fundamental Types of Data Encryption
Encryption data operates through two primary methodological approaches: symmetric and asymmetric encryption. Symmetric encryption uses a single encryption key for both encoding and decoding data, making it faster and more computationally efficient. Advanced Encryption Standard (AES), particularly AES-256, represents the gold standard in symmetric encryption, offering robust protection for large data volumes.
In contrast, asymmetric encryption utilises two distinct but mathematically linked keys: a public key for encryption and a private key for decryption. This method provides enhanced security by eliminating the need to share a single secret key between communicating parties. Research from the National Institute of Standards and Technology demonstrates that asymmetric encryption is particularly valuable for secure communication channels and digital signature verification.
Advanced Encryption Technologies
Emerging encryption technologies are expanding the boundaries of data protection. Homomorphic encryption represents a groundbreaking approach, enabling computational operations directly on encrypted data without requiring decryption. This technology is particularly revolutionary for privacy-sensitive environments such as healthcare, finance, and cloud computing, where data confidentiality is paramount.
With the anticipated rise of quantum computing, researchers are developing post-quantum cryptographic algorithms designed to withstand potential computational attacks. These advanced encryption methods aim to create quantum-resistant versions of existing standards like AES, ensuring long-term data security in an increasingly complex technological landscape.
The selection of an appropriate encryption method depends on multiple factors, including:
- Performance requirements: Processing speed and computational overhead
- Security level: Strength of encryption against potential breaches
- Computational complexity: Resources needed for encryption and decryption
- Specific use case: Application-specific security demands
Organisations must carefully evaluate their unique requirements when implementing data encryption strategies. While no single encryption method provides absolute protection, a nuanced, multi-layered approach can significantly mitigate potential security risks.
As cyber threats continue to evolve, understanding and implementing robust data encryption methods becomes increasingly crucial. By staying informed about technological advancements and adopting comprehensive security protocols, organisations can effectively protect their digital assets and maintain the confidentiality of sensitive information.
Why Data Encryption is Crucial
In an increasingly digital world, data encryption has transformed from a technical recommendation to an absolute necessity for organisations across all sectors. The proliferation of cyber threats, stringent regulatory requirements, and the escalating value of digital information have made encryption a critical shield protecting sensitive data from malicious intrusion.
Financial and Reputational Risk Mitigation
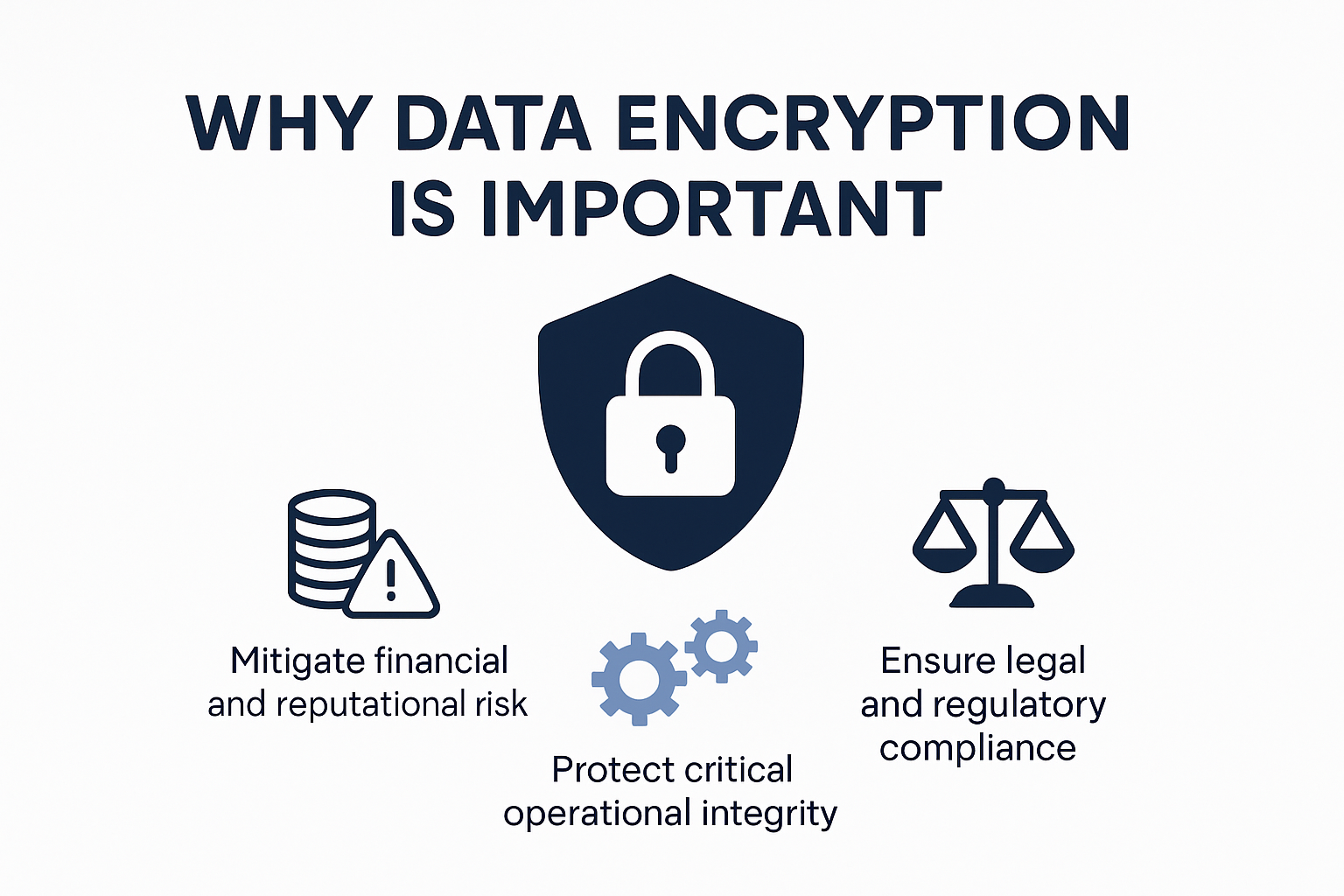
Data breaches can devastate organisations financially and reputionally. Research indicates that seven million unencrypted data records are compromised every day, representing a staggering potential for economic loss. A single security incident can result in substantial direct costs, including forensic investigations, system repairs, and potential legal settlements.
Moreover, the reputational damage from a data breach can be far more devastating than immediate financial losses. Customers rapidly lose trust in organisations that fail to protect their personal information, potentially leading to long-term brand erosion and customer attrition. Encryption serves as a critical first line of defence, demonstrating an organisation’s commitment to robust cybersecurity practices.
Legal and Regulatory Compliance
Regulatory landscapes worldwide are increasingly mandating stringent data protection measures. The European Union’s General Data Protection Regulation (GDPR) exemplifies this trend, imposing severe penalties for non-compliance with encryption standards. Organisations can face fines up to €20 million or 4% of their annual global turnover for inadequate data protection mechanisms.
Beyond financial penalties, legal non-compliance can trigger comprehensive investigations, potential litigation, and significant operational disruptions. By implementing robust encryption strategies, organisations not only protect their data but also demonstrate proactive compliance with evolving regulatory frameworks.
Protecting Critical Operational Integrity
Data encryption extends far beyond mere information protection; it ensures the integrity and reliability of critical operational systems. In sensitive sectors like healthcare, encrypted data prevents potentially life-threatening medical decision errors. Manufacturing, logistics, and financial services similarly rely on encrypted data to maintain accurate operational records and prevent unauthorized manipulations.
Cyber attackers continuously develop sophisticated techniques to exploit vulnerabilities. Encryption acts as a dynamic, adaptive defence mechanism that transforms readable data into complex, unreadable formats. This transformation significantly increases the complexity and resources required for successful cyber intrusions.
![]()
Key considerations for understanding encryption’s crucial role include:
- Data confidentiality: Preventing unauthorized access to sensitive information
- Operational resilience: Maintaining system integrity during potential cyber incidents
- Regulatory adherence: Meeting complex legal requirements across different jurisdictions
- Customer trust: Demonstrating a commitment to robust security practices
Organisations must view data encryption not as an optional security layer but as a fundamental operational requirement. The potential consequences of inadequate data protection far outweigh the investment required to implement comprehensive encryption strategies.
As digital transformation accelerates and cyber threats become increasingly sophisticated, data encryption remains a non-negotiable component of modern organisational security. By prioritising encryption, businesses can protect their most valuable assets, maintain regulatory compliance, and preserve the trust of their stakeholders in an unpredictable digital landscape.
Practical Data Encryption Applications
Data encryption transcends theoretical concepts, playing a pivotal role in real-world applications across diverse sectors. By transforming sensitive information into secure, unreadable formats, encryption enables organisations to protect critical digital assets and maintain operational confidentiality.
Healthcare and Patient Data Protection
Healthcare organisations increasingly leverage advanced encryption techniques to safeguard patient records and meet stringent regulatory requirements. End-to-end and field-level encryption methods ensure that sensitive medical information remains protected throughout its lifecycle, preventing unauthorized access and potential data breaches.
Specialised encryption approaches, such as homomorphic encryption, enable medical researchers to perform complex data analyses without compromising patient privacy. This revolutionary technology allows computational operations on encrypted data, supporting critical research while maintaining individual confidentiality.
Financial Services and Secure Transactions
In the financial sector, encryption is fundamental to maintaining transaction integrity and protecting customer information. Advanced encryption techniques are critical for securing biometric data in modern payment systems, particularly as these platforms increasingly incorporate artificial intelligence and big data analytics for authentication processes.
Cryptographic protocols protect everything from online banking transactions to cryptocurrency exchanges, ensuring that financial data remains confidential and tamper-proof. Multi-factor authentication combined with robust encryption creates multiple layers of security, significantly reducing the risk of fraudulent activities.
Government and Enterprise Data Security
Homomorphic encryption supports privacy-preserving data analysis across government and enterprise environments, enabling secure computational processes without exposing raw data. This technology is particularly valuable in scenarios requiring collaborative research, intelligence gathering, and cross-departmental data sharing while maintaining strict confidentiality.
Enterprise applications of encryption extend beyond traditional data protection, encompassing:
- Cloud storage security: Protecting sensitive corporate information stored on remote servers
- Communication platforms: Securing email, messaging, and video conferencing systems
- Supply chain management: Maintaining confidentiality of logistics and procurement data
- Intellectual property protection: Safeguarding proprietary research and development information
Organisations must adopt a holistic approach to encryption, recognising that different applications require tailored encryption strategies. The complexity of encryption methods should align with the sensitivity and specific requirements of the data being protected.
As technological landscapes evolve, encryption will continue to adapt, integrating emerging technologies like quantum-resistant algorithms and advanced machine learning techniques. By staying ahead of potential security threats, organisations can create robust, dynamic encryption frameworks that protect their most valuable digital assets.
Ultimately, practical data encryption is not just about preventing unauthorized access; it’s about creating a secure, trustworthy digital environment where information can be shared, analysed, and utilised with confidence and peace of mind.
Implementing Effective Encryption Strategies
Developing robust encryption strategies requires a comprehensive, multi-layered approach that adapts to evolving technological landscapes and emerging cyber threats. Organisations must move beyond simplistic protection mechanisms and embrace sophisticated, dynamic encryption frameworks that address complex security challenges.
Comprehensive Encryption Architecture
The most effective encryption strategies combine strong symmetric and asymmetric algorithms, creating a comprehensive security ecosystem. Advanced implementations integrate AES-256 symmetric encryption for high-performance data protection, complemented by RSA-4096 asymmetric algorithms to secure key exchanges and digital signatures.
Key management represents a critical component of successful encryption strategies. Organisations must implement rigorous controls that restrict encryption key access, rotate keys regularly, and maintain secure, isolated storage environments. This approach minimises potential vulnerabilities and ensures that even if one layer of security is compromised, additional protective mechanisms remain intact.
Multi-Dimensional Protection Approach
Implementing effective encryption requires a holistic security framework that extends beyond traditional encryption techniques. Critical elements include:
- Encryption of data at rest, in transit, and during processing
- Multi-factor authentication mechanisms
- Regular security software updates
- Consistent and encrypted data backups
- Routine security audits and vulnerability assessments
Organisations must adopt a Zero Trust architecture, assuming no inherent trust within their digital ecosystem. This approach mandates continuous verification of every access request, regardless of its origin, significantly reducing potential breach risks.
Future-Proofing Encryption Strategies
As quantum computing emerges, organisations are proactively adopting post-quantum cryptography to safeguard against advanced computational threats. These emerging encryption methodologies develop algorithms resistant to potential quantum computational attacks, ensuring long-term data protection in an increasingly complex technological landscape.
End-to-end encryption integrated within Zero Trust frameworks represents the cutting edge of data protection strategies. By implementing encryption at every potential vulnerability point, organisations can create adaptive, resilient security architectures that dynamically respond to emerging threats.
Successful encryption implementation requires continuous education and awareness. Technology teams must stay informed about latest encryption technologies, potential vulnerabilities, and emerging best practices. Regular training programmes ensure that personnel understand the critical role of encryption in maintaining organisational security.
The economic investment in comprehensive encryption strategies should be viewed as a strategic asset rather than a cost centre. The potential financial and reputational damages from data breaches far outweigh the resources required to develop and maintain robust encryption frameworks.
As digital transformation accelerates and cyber threats become increasingly sophisticated, encryption transforms from a technical recommendation to an absolute operational necessity. Organisations that prioritise intelligent, adaptive encryption strategies will be best positioned to protect their most valuable digital assets in an unpredictable global landscape.
Frequently Asked Questions
What is data encryption?
Data encryption is the process of converting readable data into an unreadable format to protect it from unauthorised access and cyber threats. It employs algorithms and keys to ensure that only authorised users can access the original information.
Why is data encryption important for organisations?
Data encryption is crucial for organisations as it safeguards sensitive information, mitigates financial and reputational risks, ensures compliance with legal regulations, and protects the integrity of critical operational systems.
What are the types of data encryption?
The two primary types of data encryption are symmetric encryption, which uses a single key for both encryption and decryption, and asymmetric encryption, which uses a pair of mathematically linked keys—a public key for encryption and a private key for decryption.
How can organisations implement effective encryption strategies?
Organisations can implement effective encryption strategies by developing a comprehensive encryption architecture that combines strong symmetric and asymmetric algorithms, adhering to a multi-dimensional protection approach, and future-proofing against emerging threats such as quantum computing.
Secure Your Future with Comprehensive Encryption Solutions
In today’s digital landscape, where seven million unencrypted data records are compromised daily, effective data encryption is no longer just a recommendation—it’s a necessity. Organisations grappling with the implications of data breaches face not only hefty fines but also the daunting task of rebuilding customer trust. As highlighted in our recent article, the financial and reputational risks associated with inadequate data protection can be overwhelming.
At Re-Solution, we understand these challenges thoroughly. With over 35 years of expertise in IT infrastructure and security, we offer tailored Managed IT Services, Network as a Service (NaaS), and Security and Compliance Solutions that ensure your sensitive information is adequately protected. We empower educational institutions, manufacturing companies, and hospitality businesses by facilitating robust connectivity and compliance across all their operations. Don’t leave your organisation vulnerable—protect your digital assets NOW. Visit us at https://re-solution.co.uk and take the first step towards securing your data with innovative encryption strategies designed to meet your specific needs.
