
Cybersecurity has become a cornerstone of modern business operations. With cyber attacks increasing by over 50 percent in recent years, the stakes have never been higher. But here’s the kicker: most companies still treat cybersecurity as just another IT issue. The truth is, it needs to be an essential part of the organisational culture. Embracing this reality is not just a safeguard; it’s a competitive advantage that can define success in a digital world.
Table of Contents
- Understanding Foundational Cybersecurity Principles
- Implementing Essential Security Measures
- Real-World Cybersecurity Scenarios Explained
- [Emerging Technological Threat Landscapes](#emerging-technological-threat- بعد landscapes)
- Ransomware And Organisational Resilience
- Human-Centric Cybersecurity Challenges
- Continuous Learning In Cybersecurity
Quick Summary
| Takeaway | Explanation |
|---|---|
| Adopt Zero Trust Architecture | Implement a zero-trust security model that verifies all users and devices at every interaction to enhance organisational security. |
| Prioritise Human Factors | Embed cybersecurity into organisational culture by fostering vigilance, accountability, and comprehensive security training for all employees. |
| Implement Continuous Network Monitoring | Develop proactive monitoring strategies that involve real-time threat detection and regular vulnerability assessments to mitigate risks effectively. |
| Integrate Continuous Learning | Transform learning into an ongoing process by embedding it into daily workflows, utilising advanced technologies, and encouraging cross-functional collaboration. |
| Prepare for Emerging Threats | Stay informed about evolving technologies and their associated risks, such as AI-driven attacks and IoT vulnerabilities, to strengthen overall cybersecurity resilience. |
 |
Understanding Foundational Cybersecurity Principles
Cybersecurity is no longer a peripheral concern but a critical strategic imperative for organisations across all sectors. At its core, cybersecurity is about protecting digital assets, systems, and networks from malicious attacks, data breaches, and unauthorized access.
The Core Architecture of Cybersecurity Defence
Understanding cybersecurity essentials begins with recognizing the fundamental architecture of digital defence. Modern cybersecurity is not a single solution but a comprehensive, multi-layered approach that integrates technological tools, human expertise, and strategic processes. The World Economic Forum’s Global Cybersecurity Outlook emphasizes that organisational resilience hinges on developing adaptive, proactive cybersecurity strategies.
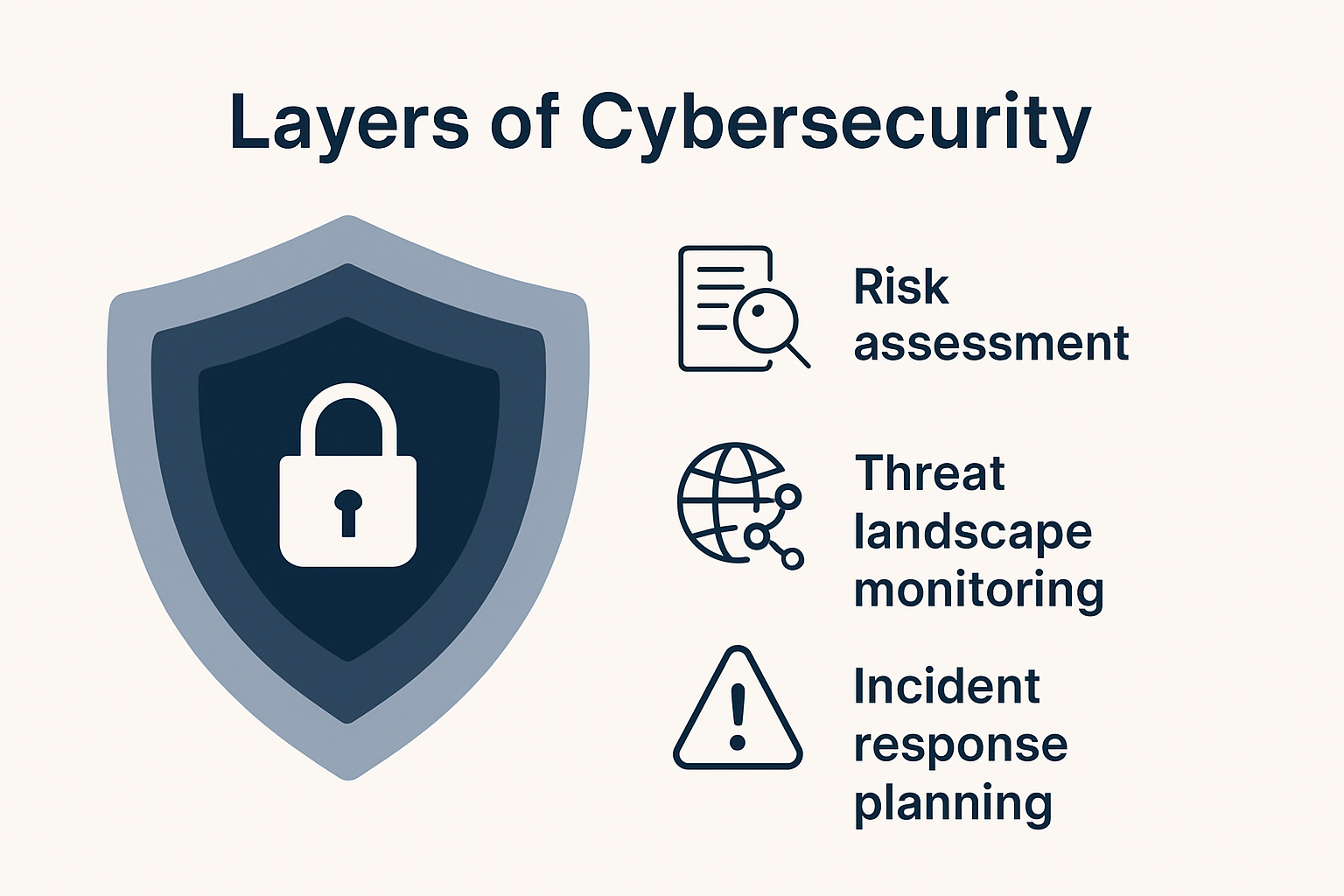
The foundational principles encompass several critical dimensions:
- Risk Assessment: Systematically identifying and evaluating potential vulnerabilities in digital infrastructure
- Threat Landscape Monitoring: Continuously tracking emerging cyber threats and attack vectors
- Incident Response Planning: Developing robust protocols for quick and effective response to potential security breaches
Human Factors in Cybersecurity
Contrary to popular belief, cybersecurity is not exclusively a technological challenge but a human-centric discipline. Research from KPMG underscores that embedding cybersecurity into organisational culture is paramount. This means transforming every employee from a potential vulnerability into a proactive defence mechanism.
Key human-focused strategies include:
- Comprehensive security awareness training
- Creating a culture of vigilance and personal accountability
- Developing clear communication channels for reporting potential security incidents
Strategic Integration of Cybersecurity Principles
Effective cybersecurity goes beyond implementing isolated tools and technologies. It requires a holistic, integrated approach that aligns technological solutions with organisational objectives. World-leading cybersecurity experts recommend a strategic framework that:
- Prioritizes continuous learning and adaptation
- Establishes clear governance and accountability structures
- Promotes cross-functional collaboration in managing cyber risks
Organisations must view cybersecurity as a dynamic, evolving discipline that requires ongoing investment, education, and strategic thinking. By understanding and implementing these foundational principles, businesses can build robust, resilient digital defence mechanisms that protect their most valuable assets in an increasingly complex technological landscape.
Implementing Essential Security Measures
In the rapidly evolving digital landscape, implementing robust security measures is not just a recommendation but a critical necessity for organisational survival. Cybersecurity is no longer about building impenetrable walls but creating adaptive, intelligent defence mechanisms that can anticipate, detect, and neutralize potential threats.
Zero Trust Architecture: A New Security Paradigm
Cisco’s Cybersecurity Readiness Index highlights a transformative approach to security: the zero-trust model. This revolutionary strategy operates on a fundamental principle: trust nothing, verify everything. Unlike traditional perimeter-based security models, zero trust assumes no user, device, or network connection is inherently safe.
Key components of zero trust implementation include:
- Continuous Authentication: Verifying user identity and device integrity at every interaction
- Micro-segmentation: Dividing network resources into smaller, isolated segments
- Least Privilege Access: Granting users minimum necessary permissions
Advanced Identity and Access Management
The World Economic Forum’s Global Cybersecurity Outlook emphasizes the critical role of sophisticated identity management. Modern security strategies must go beyond traditional password protocols, integrating intelligent, multi-layered authentication mechanisms.
Effective identity and access management strategies include:
- Implementing multi-factor authentication
- Utilizing biometric verification technologies
- Deploying AI-powered anomaly detection systems
- Creating comprehensive identity visibility frameworks
Proactive Network Defence and Monitoring
KPMG’s Cybersecurity Considerations underscores the importance of continuous network monitoring and proactive threat management. Security is no longer a static defence but a dynamic, real-time intelligence system that anticipates and neutralizes potential breaches.
Critical network defence strategies encompass:
- Regular vulnerability scanning and assessment
- Implementing advanced threat detection algorithms
- Creating comprehensive security event monitoring protocols
- Developing rapid incident response mechanisms
Successful security implementation requires a holistic approach that integrates technological solutions, human expertise, and strategic thinking. By adopting these advanced security measures, organisations can transform potential vulnerabilities into robust, adaptive defence mechanisms capable of protecting critical digital assets in an increasingly complex technological environment.
Real-World Cybersecurity Scenarios Explained
Cybersecurity is no longer an abstract concept but a critical reality that impacts organisations across every sector. Understanding real-world scenarios provides invaluable insights into how cyber threats manifest and how organisations can effectively respond and mitigate risks.
Emerging Technological Threat Landscapes
The World Economic Forum’s Global Cybersecurity Outlook reveals that emerging technologies are creating unprecedented cybersecurity challenges. Artificial intelligence, genetic engineering, and advanced semiconductor technologies are transforming the threat landscape, introducing complex vulnerabilities that traditional security models struggle to address.
Key emerging technological threat scenarios include:
- AI-Driven Attacks: Sophisticated machine learning algorithms capable of developing adaptive malware
- Quantum Computing Vulnerabilities: Potential for breaking current encryption methodologies
- Internet of Things (IoT) Ecosystem Risks: Exponentially increasing attack surfaces through interconnected devices
Ransomware And Organisational Resilience
UC Berkeley’s Cybersecurity Futures 2025 project highlights that modern cybersecurity challenges involve more complex actors with increasingly sophisticated motivations. Ransomware attacks have evolved from simple data encryption to complex, multi-stage operations targeting critical infrastructure and organisational operations.
Critical ransomware scenario characteristics include:
- Targeting specific organisational vulnerabilities
- Implementing multi-layered extortion strategies
- Exploiting human psychological factors
- Leveraging geopolitical tensions for strategic disruption
Human-Centric Cybersecurity Challenges
Understanding cybersecurity requires recognizing that technological solutions are fundamentally human challenges. Research from Berkeley’s Center for Long-Term Cybersecurity emphasizes that future cyber threats will increasingly involve complex interactions between technological systems and human behaviours.
Key human-centric cybersecurity scenarios include:
- Social engineering attacks manipulating psychological triggers
- Insider threats from disgruntled or compromised employees
- Global talent movement creating unpredictable knowledge transfer risks
- Cultural and ethical challenges in managing digital identities
Navigating these complex scenarios requires a holistic approach that combines technological sophistication, human understanding, and strategic adaptability. Organisations must develop flexible, intelligent cybersecurity frameworks that can anticipate, respond, and learn from emerging threats in real-time.
Continuous Learning in Cybersecurity
In the dynamic world of cybersecurity, knowledge is not just power—it’s survival. The rapid evolution of technological threats demands a fundamental shift from traditional, static learning models to continuous, adaptive learning strategies that keep professionals ahead of emerging challenges.
Transforming Learning Paradigms
Cybersecurity Intelligence Research highlights that modern cybersecurity learning transcends periodic training sessions. Organizations must embed learning directly into daily workflows, creating an environment where continuous skill development becomes an intrinsic part of professional practice.
Key transformation strategies include:
- Personalized Learning Pathways: Tailoring educational content to individual skill levels and roles
- Real-Time Threat Intelligence Integration: Connecting learning modules with current global cyber threat landscapes
- Cross-Functional Knowledge Sharing: Encouraging interdepartmental learning and collaboration
Advanced Learning Technologies
Paubox’s Cybersecurity Training Insights reveal that by 2025, learning technologies will dramatically reshape cybersecurity education. Emerging technologies like AI-driven personalization and immersive extended reality (XR) simulations are revolutionizing how professionals acquire and retain critical security skills.
Cutting-edge learning technology components include:
- AI-powered adaptive learning platforms
- Microlearning modules for targeted skill development
- Extended reality (XR) attack scenario simulations
- Gamified learning experiences that enhance engagement
Cultivating a Learning Culture
Continuous learning in cybersecurity is more than technological tools—it’s about developing an organisational mindset of perpetual curiosity and adaptability. Cybersecurity Intelligence Research emphasizes that successful cybersecurity teams cultivate a culture where learning is viewed as a strategic imperative, not an occasional requirement.
Essential cultural development strategies include:
- Encouraging proactive knowledge seeking
- Rewarding innovative problem-solving approaches
- Creating safe environments for discussing potential vulnerabilities
- Establishing mentorship and peer-learning networks
The future of cybersecurity learning is dynamic, interconnected, and continuously evolving. By embracing adaptive learning technologies, fostering a culture of curiosity, and integrating knowledge development into daily practices, organisations can build resilient, responsive cybersecurity capabilities that can effectively navigate the complex threat landscapes of tomorrow.
Frequently Asked Questions
What are the foundational principles of cybersecurity?
Cybersecurity foundational principles include risk assessment, threat landscape monitoring, and incident response planning. These principles help organisations protect their digital assets and build robust security strategies.
How does Zero Trust Architecture improve cybersecurity?
Zero Trust Architecture enhances cybersecurity by assuming that no user or device is inherently trustworthy. It requires continuous authentication and minimal access privileges, significantly reducing the risk of breaches.
Why is human factor crucial in cybersecurity?
The human factor is crucial in cybersecurity because employees can be the weakest link or the strongest defence. By fostering a culture of vigilance and accountability through security awareness training, organisations empower employees to actively participate in their cybersecurity defence.
What strategies can organisations employ for continuous learning in cybersecurity?
Organisations can employ strategies like personalised learning pathways, real-time threat intelligence integration, and encouraging cross-functional knowledge sharing. These strategies ensure that cybersecurity professionals remain updated on evolving threats and best practices.
Strengthen Your Cyber Resilience with Re-Solution
In the ever-evolving landscape of cybersecurity, staying ahead of threats like ransomware and AI-driven attacks is paramount. The insights from Your Guide to Cybersecurity Essentials 2025 underscore the critical need for a Zero Trust Architecture and continuous learning. Are you equipped to foster a culture of security within your organization and implement cutting-edge measures to protect your assets?
At Re-Solution, we specialize in Managed IT Services and Security & Compliance Solutions designed to transform your cybersecurity strategy. With over 35 years of experience as a trusted Cisco partner, we provide tailored solutions that enhance connectivity and resilience across sectors including education, manufacturing, and hospitality.
Don’t wait for a cyber incident to take action! Visit https://re-solution.co.uk today to discuss how we can empower your organisation to navigate emerging threats and foster a robust cybersecurity culture. Together, let’s secure your digital future.
