![]()
Data protection is more crucial than ever as we approach 2025. The rapid evolution of cyber threats continues to put sensitive information at risk. Did you know that 90 percent of data breaches are caused by human error? But here’s the twist: most organisations focus solely on technology solutions, ignoring the fundamental role of employee training and awareness. To truly safeguard data, a multi-faceted approach that includes empowering your workforce is essential.
Table of Contents
- How To Plan Your Data Protection Strategy
- Implementing Key Data Protection Protocols
- Maintaining Strong Data Security Practices
- Responding Effectively To Data Breaches
Quick Summary
| Takeaway | Explanation |
|---|---|
| Comprehensive Risk Assessment is Essential | Organisations must conduct thorough risk assessments and data mapping to identify data assets, their locations, and vulnerabilities, tailoring protection strategies accordingly. |
| Adopt a Multi-Layered Protection Approach | Implementing a multi-layered strategy that includes advanced encryption, regular security patch management, and continuous employee training enhances resilience against data breaches. |
| Continuous Monitoring is Key | Establishing a routine for quarterly security assessments and real-time monitoring of data access helps maintain compliance and protects sensitive information effectively. |
| Employee Training is Crucial | Comprehensive cybersecurity training transforms employees into active defenders, significantly reducing human-related security vulnerabilities. |
| Develop a Robust Incident Response Plan | Quick and coordinated incident response strategies, including evidence preservation and communication channels, are essential for effectively managing data breaches. |
How to Plan Your Data Protection Strategy
Planning a robust data protection strategy is crucial for organisations across various sectors, from educational institutions to manufacturing companies. The increasing complexity of digital landscapes and evolving cyber threats demand a comprehensive and proactive approach to safeguarding sensitive information.
Comprehensive Risk Assessment and Data Mapping
Before implementing any data protection measures, organisations must conduct a thorough risk assessment. This process involves identifying and understanding all data assets, their locations, and potential vulnerabilities. According to Hawkshield AI’s research, implementing a comprehensive data security management strategy that includes data classification procedures, access controls, and role definitions can significantly reduce system vulnerabilities.
Begin by creating a detailed inventory of your data, including:
- Types of data collected and stored
- Data storage locations (cloud, on-premises, hybrid)
- Current access permissions
- Potential exposure points
This mapping exercise enables organisations to develop targeted protection strategies tailored to their specific data ecosystem.
Implementing Multi-Layered Protection Mechanisms
Effective data protection requires a multi-layered approach that goes beyond traditional perimeter defences. This strategy should encompass technological solutions, organisational policies, and human behaviour management. HYCU’s research emphasises adopting a “Protection Without Boundaries” approach to adapt to the evolving data protection landscape.
Key components of a multi-layered protection strategy include:
- Advanced encryption technologies
- Regular security patch management
- Robust authentication mechanisms
- Continuous employee training programmes
- Incident response and recovery plans
By implementing these mechanisms, organisations can create a resilient defence against potential data breaches and cyber threats.
Continuous Monitoring and Compliance Management
Data protection is not a one-time effort but an ongoing process requiring constant vigilance. Regular audits and assessments are essential for maintaining the effectiveness of your data protection strategy. Alation’s compliance research highlights the importance of conducting systematic reviews to ensure adherence to regulatory requirements.
Establish a routine that includes:
- Quarterly security assessments
- Annual comprehensive risk evaluations
- Real-time monitoring of data access and potential anomalies
- Regular updates to security protocols based on emerging threats
By treating data protection as a dynamic, evolving process, organisations can stay ahead of potential risks and maintain the integrity of their sensitive information. Remember, a well-planned data protection strategy is not just about preventing breaches, but about building a culture of security and trust within your organisation.
Implementing Key Data Protection Protocols
Implementing robust data protection protocols is essential for organisations seeking to safeguard their critical information assets in an increasingly complex digital landscape. Beyond basic security measures, modern data protection requires sophisticated, multi-dimensional approaches that address technological, operational, and strategic challenges.
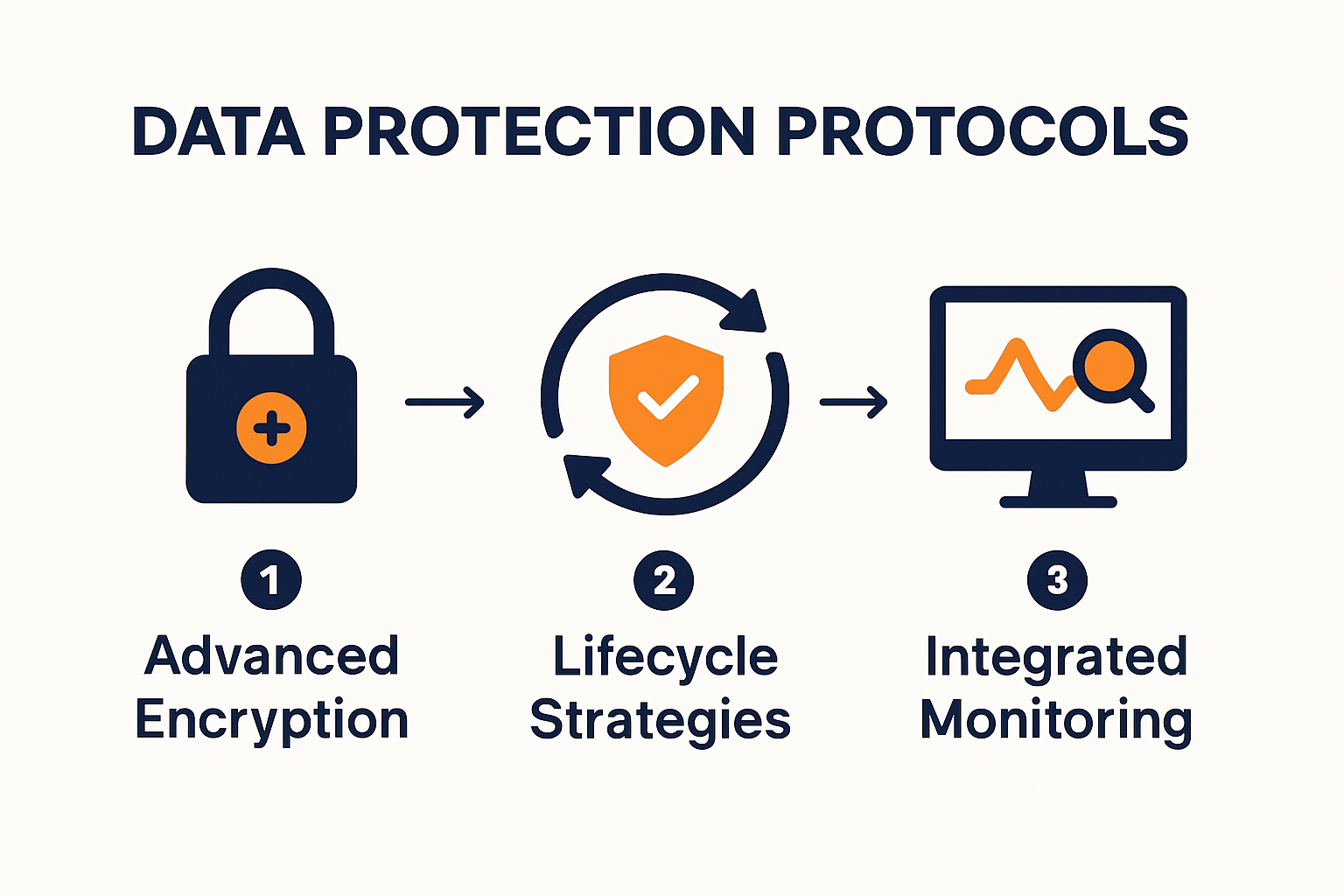
Advanced Encryption and Privacy-Enhancing Technologies
In 2025, organisations must move beyond traditional encryption methods and embrace advanced Privacy-Enhancing Technologies (PETs). According to TrustCloud Community Research, emerging technologies like Homomorphic Encryption, Federated Learning, and Differential Privacy are becoming critical for maintaining data privacy while enabling meaningful insights.
Key encryption protocols to implement include:
- AES-256 Encryption: For comprehensive data protection at rest and in transit
- RSA-4096 Public Key Infrastructure: Ensuring secure communication channels
- Zero-Knowledge Proof Protocols: Verifying data authenticity without revealing sensitive information
These advanced technologies allow organisations to protect data integrity while maintaining operational flexibility, enabling secure data processing and analysis across various platforms and environments.
Lifecycle Data Protection Strategies
Effective data protection extends far beyond initial security implementations. Storage Networking Industry Association (SNIA) research emphasises the critical importance of protecting data throughout its entire lifecycle.
Comprehensive lifecycle protection involves:
- Data Creation Stage: Implementing secure input mechanisms
- Storage Stage: Utilising advanced encryption and access controls
- Transmission Stage: Securing communication channels
- Archival Stage: Maintaining long-term data integrity and confidentiality
- Destruction Stage: Ensuring complete and verifiable data elimination
By adopting a holistic approach, organisations can minimise vulnerabilities and maintain consistent data protection standards across all operational phases.
Integrated Compliance and Monitoring Frameworks
Modern data protection protocols require dynamic, real-time monitoring and adaptive compliance mechanisms. Organisations must develop integrated frameworks that combine technological solutions with continuous assessment and rapid response capabilities.
Key components of an integrated framework include:
- Automated threat detection systems
- Continuous compliance monitoring tools
- Machine learning-powered anomaly detection
- Comprehensive audit trail mechanisms
- Rapid incident response protocols
These integrated frameworks enable organisations to detect, respond to, and mitigate potential security risks proactively, transforming data protection from a reactive to a predictive discipline.
Implementing robust data protection protocols is not just a technical requirement but a strategic imperative. By embracing advanced technologies, comprehensive lifecycle strategies, and integrated monitoring frameworks, organisations can build resilient, future-proof data protection ecosystems that safeguard their most valuable digital assets.
Maintaining Strong Data Security Practices
Maintaining robust data security practices is a continuous, dynamic process that requires consistent attention, strategic planning, and adaptive technologies. As digital landscapes evolve, organisations must develop comprehensive approaches that go beyond traditional security measures to protect their most critical information assets.

Employee Training and Cybersecurity Awareness
Human factors remain the most significant vulnerability in data security strategies. TrustArc’s Data Privacy Guide emphasises the critical importance of comprehensive cybersecurity training and awareness programmes that transform employees from potential security risks into active defenders of organisational data.
Effective training programmes should include:
- Phishing Recognition: Teaching employees to identify and report suspicious communication
- Password Management: Implementing strong password creation and management protocols
- Device Security: Understanding risks associated with personal and work devices
- Data Handling Procedures: Clear guidelines for managing sensitive information
By creating a culture of security awareness, organisations can significantly reduce human-related security vulnerabilities and build a proactive defence mechanism.
AI Governance and Algorithmic Risk Management
With the rapid advancement of artificial intelligence, organisations must develop robust AI governance frameworks. TrustArc’s research highlights the necessity of implementing rigorous assessments for privacy, bias, and compliance risks associated with AI tools and algorithms.
Key components of AI governance include:
- Algorithmic Transparency: Ensuring clear understanding of AI decision-making processes
- Bias Detection: Regular audits to identify and mitigate potential algorithmic biases
- Privacy Impact Assessments: Comprehensive evaluations of AI system data usage
- Ethical AI Development: Establishing guidelines for responsible AI implementation
By proactively managing AI-related risks, organisations can harness technological innovations while maintaining stringent data protection standards.
Advanced Technical Security Implementations
Beyond training and governance, organisations must continuously upgrade their technical security infrastructure. Cybersecurity Innovation Research recommends implementing multi-layered security approaches that combine advanced technologies and adaptive strategies.
Critical technical security implementations include:
- Zero Trust Architecture: Eliminating automatic trust within network environments
- Advanced Endpoint Protection: Utilising machine learning-powered threat detection
- Multi-Factor Authentication: Implementing sophisticated access verification mechanisms
- Continuous Network Monitoring: Real-time threat detection and rapid response systems
These technical measures create a comprehensive, adaptive security ecosystem that can respond dynamically to emerging digital threats.
Maintaining strong data security practices is not a destination but a continuous journey. Organisations must remain agile, informed, and proactive, recognising that security is an ongoing process requiring constant vigilance, adaptation, and investment in both technological solutions and human capabilities.
Responding Effectively to Data Breaches
Data breaches represent a critical operational challenge that demands swift, strategic, and comprehensive response mechanisms. Despite robust preventative measures, organisations must be prepared to act decisively when unexpected security incidents occur, minimising potential damage and maintaining stakeholder trust.
Immediate Incident Response and Containment
BakerHostetler’s 2025 Data Security Incident Response Report emphasises the importance of rapid, coordinated response strategies. Organisations must assemble a multidisciplinary breach response team comprising forensics experts, legal counsel, information security professionals, IT specialists, operations managers, human resources representatives, communications experts, and senior management.
Critical immediate response steps include:
- Isolate Affected Systems: Immediately disconnect compromised network segments
- Preserve Evidence: Capture forensic data without disrupting potential investigation materials
- Activate Incident Response Plan: Execute pre-defined emergency protocols
- Establish Communication Channels: Create secure communication mechanisms for the response team
The first 24-48 hours are crucial in determining the potential scale and impact of a data breach, making rapid, methodical action essential.
Comprehensive Breach Investigation and Vulnerability Analysis
Following initial containment, organisations must conduct a thorough, systematic investigation to understand the breach’s root causes, extent, and potential long-term implications. The Federal Trade Commission’s Breach Response Guide recommends a comprehensive forensic analysis that goes beyond immediate technical assessments.
Key investigation components include:
- Forensic Data Analysis: Detailed examination of breach mechanisms and entry points
- Vulnerability Mapping: Identifying systemic weaknesses that enabled the breach
- Data Impact Assessment: Determining the scope of potentially compromised information
- Threat Actor Profiling: Understanding potential motivations and origins of the security incident
This investigative phase provides critical insights for both immediate remediation and long-term security strategy development.
Stakeholder Communication and Recovery Strategy
Effective communication is paramount during and after a data breach. Organisations must develop transparent, timely communication strategies that rebuild trust while demonstrating comprehensive response capabilities. UpGuard’s Cybersecurity Recommendations highlight the importance of proactive, clear communication with affected stakeholders.
Communication and recovery strategies should encompass:
- Regulatory Notification: Prompt reporting to relevant authorities
- Customer Communication: Clear, honest disclosure of breach details and potential impacts
- Remediation Offerings: Providing support such as credit monitoring or identity protection
- Ongoing Transparency: Regular updates about investigation and prevention efforts
Additionally, organisations must develop a robust recovery plan that addresses:
- Security infrastructure improvements
- Employee retraining
- Enhanced monitoring protocols
- Potential legal and regulatory implications
Responding effectively to data breaches requires a holistic approach that balances technical expertise, strategic communication, and continuous learning. By developing comprehensive, adaptable response mechanisms, organisations can transform potential catastrophic incidents into opportunities for demonstrating resilience, transparency, and commitment to stakeholder protection.
Frequently Asked Questions
What are the key components of a data protection strategy for 2025?
A robust data protection strategy should include comprehensive risk assessment, multi-layered protection mechanisms, continuous monitoring, employee training, and a well-defined incident response plan.
How can organisations minimise human error in data protection?
Organisations can reduce human error by implementing regular cybersecurity training, promoting awareness of phishing attacks, and establishing clear data handling procedures for employees.
What technologies should be adopted for advanced data protection?
Emerging technologies such as advanced encryption methods (e.g., AES-256, RSA-4096) and Privacy-Enhancing Technologies (like Homomorphic Encryption) should be adopted to safeguard sensitive data effectively.
How should organisations respond to a data breach?
An effective response to a data breach involves immediate incident containment, a comprehensive forensic investigation, and transparent communication with stakeholders regarding the breach and its implications.
Elevate Your Data Protection Strategy with Re-Solution
In a world where 90 percent of data breaches stem from human error, it’s not enough to rely solely on technology for data protection. You need a holistic approach that combines robust IT infrastructure with an empowered workforce. Thankfully, Re-Solution stands ready to be your partner on this critical journey, offering tailored solutions that encompass everything from managed IT services to comprehensive security frameworks.
Imagine achieving peace of mind. With our expertise in Network as a Service (NaaS) and proactive infrastructure audits, we help organisations like yours build a resilient defence against cyber threats while enhancing compliance and connectivity. Don’t wait for a breach to happen! Equip your team with the right tools and knowledge to safeguard critical data today. Explore how our award-winning solutions can transform your approach to data protection at https://re-solution.co.uk. Take the first step towards a secure digital future—because protecting your data is our priority, and your success is our mission.
