
Understanding your network is more important than ever in our digitally connected world. Did you know that 62 percent of data breaches happen due to compromised user credentials? It’s startling, but it gets even more interesting. Most people think the hardware is the biggest risk in a network. However, the true danger lies in poor security practices and a lack of awareness. With the right knowledge and proactive measures, you can transform your home network into a secure fortress.
Table of Contents
Quick Summary
| Takeaway | Explanation |
|---|---|
| Understand Key Components | Familiarise yourself with the physical (hardware) and logical (software) components of your network to ensure effective communication and security measures. |
| Implement Strong Security Configurations | Establish robust foundational security practices, including changing default router credentials, keeping firmware updated, and modifying the default network name. |
| Utilise Effective Data Transmission Methods | Recognise the importance of packet-based transmission, multipath strategies, and the distinctions between wired and wireless technologies for optimising network performance. |
| Monitor Your Network Continuously | Conduct regular device audits, monitor traffic for suspicious activities, and configure firewalls to strengthen overall network security and resilience against threats. |
What are the key Components?
Understanding your network requires a comprehensive grasp of its fundamental building blocks. These key components form the backbone of any robust network infrastructure, enabling seamless communication and data transfer across various systems and devices.
Physical Network Infrastructure
The foundation of any network lies in its physical infrastructure. This critical layer includes hardware devices that form the tangible framework of network connectivity. Network devices play a crucial role in establishing and maintaining communication channels. Routers, switches, cables, and network interface cards (NICs) represent the primary physical components that enable data transmission.
According to research from IEEE, the physical layer of network architecture is responsible for the actual transmission of raw bits between network nodes. This layer encompasses various critical elements:
- Cables and Connectors: Ethernet cables, fiber optic lines, and wireless transmission mediums
- Network Hardware: Routers, switches, hubs, and access points
- Transmission Media: Wired and wireless communication channels
Logical Network Components
Beyond the physical infrastructure, logical components form the intellectual framework of network communication. These software-based elements manage data flow, security, and network protocols. The Network Layer and Transport Layer are particularly crucial in understanding your network’s operational mechanics.
Key logical components include:
- Network Protocols: TCP/IP, UDP, HTTP/HTTPS
- Operating Systems: Network-specific operating systems managing resource allocation
- Execution Environments: Virtual machines and application runtime environments
Security And Management Components
Network security and management represent the final critical dimension of network infrastructure. These components ensure the integrity, performance, and protection of network resources. Firewalls, intrusion detection systems, and network management software form the defensive and operational backbone of modern network architectures.
Comprehensive network management involves multiple layers of protection and monitoring:
- Access Control Systems: Authentication and authorization mechanisms
- Monitoring Tools: Performance tracking and diagnostic utilities
- Security Protocols: Encryption, threat detection, and prevention systems
Understanding your network requires a holistic approach that considers both the physical and logical components. Each element plays a vital role in creating a robust, secure, and efficient communication infrastructure. By recognizing these key components, organizations can design, implement, and maintain networks that meet their specific operational requirements.
How does your data travel?
Understanding your network’s data transmission process reveals a complex and fascinating journey that transforms digital information from its origin to its destination. Data travels through networks using sophisticated mechanisms that ensure reliable, efficient, and secure communication across various technological landscapes.
Packet-Based Transmission Mechanism
Data transmission fundamentally relies on the packet-switching technique, where information is broken down into smaller, manageable units called packets. According to research from IEEE Communications Society, each packet contains crucial routing information that enables independent navigation through network infrastructure.
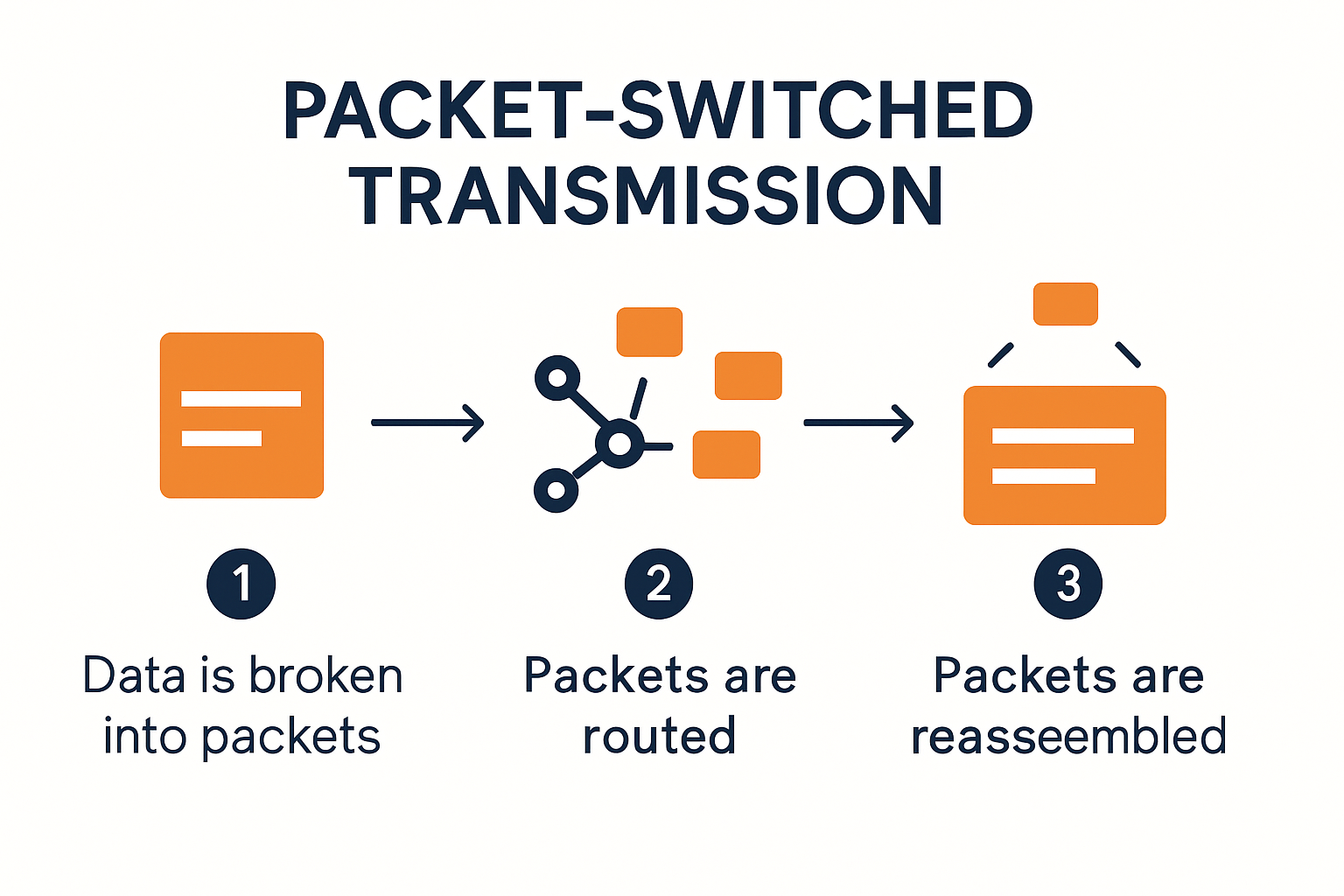
The packet transmission process involves several critical steps:
- Segmentation: Breaking large data files into smaller, transportable packets
- Addressing: Assigning unique identifiers to each packet
- Routing: Determining optimal transmission paths
- Reassembly: Reconstructing original data at the destination
Multipath Data Transmission
Advanced network studies demonstrate that modern networks utilize multipath transmission strategies to enhance data transfer efficiency. Unlike traditional single-path methods, multipath transmission allows data packets to travel through multiple network routes simultaneously, significantly improving transmission speed and reliability.
Key advantages of multipath transmission include:
- Increased Throughput: Parallel packet transmission
- Reduced Latency: Faster overall data movement
- Enhanced Redundancy: Multiple route options prevent complete transmission failure
Wireless and Wired Transmission Technologies
Network data transmission encompasses both wireless and wired technologies, each with unique characteristics and applications. Technological research highlights the diverse methods used for moving digital information across networks.
Wired transmission technologies include:
- Ethernet Cables: High-speed, stable connections
- Fiber Optic Lines: Ultra-fast, long-distance data transfer
- Coaxial Cables: Traditional medium for network connectivity
Wireless transmission methods feature:
- Wi-Fi Networks: Local area wireless connectivity
- Cellular Data Networks: Mobile and wide-area transmission
- Satellite Communication: Global network coverage
The intricate process of data transmission represents a remarkable technological achievement. By understanding how your data travels, organizations can optimize network performance, improve communication efficiency, and ensure robust, reliable digital interactions across complex technological ecosystems.

Securing your home network
Home network security represents a critical defence against potential cyber threats, protecting your personal data, devices, and digital privacy. Understanding and implementing robust security measures can significantly reduce the risk of unauthorized access and potential digital vulnerabilities.
Securing your home network begins with establishing strong foundational protections. According to guidance from the National Security Agency, several critical steps can dramatically enhance network security.
Key fundamental configurations include:
- Router Password Management: Change default router credentials to complex, unique passwords
- Firmware Updates: Regularly update router firmware to patch security vulnerabilities
- Network Name Protection: Modify default SSID to prevent easy network identification
- Administrative Access: Limit router administration to internal network connections
Wireless Network Protection
Wireless network security demands specialized attention due to the inherent vulnerabilities of radio-based transmissions. Expert recommendations emphasize implementing robust encryption and authentication mechanisms.
Critical wireless security strategies include:
- Encryption Protocols: Implement WPA3 or WPA2 with strong, complex passphrases
- Signal Management: Minimize wireless signal range beyond necessary coverage
- Guest Network Segregation: Create separate networks for visitors and IoT devices
- Disable Remote Management: Prevent external access to router configurations
Advanced Security Monitoring
Comprehensive home network security extends beyond initial configurations, requiring continuous monitoring and proactive threat detection. Cybersecurity research highlights the importance of ongoing vigilance and adaptive security practices.
Advanced security monitoring techniques involve:
- Device Inventory: Regularly audit and verify connected devices
- Traffic Monitoring: Use network monitoring tools to detect suspicious activities
- Firewall Configuration: Enable and configure robust hardware and software firewalls
- Regular Security Audits: Periodically review and update security configurations
Securing your home network is not a one-time event but a continuous process of assessment, adaptation, and implementation. By understanding potential vulnerabilities and adopting a comprehensive security approach, individuals can create resilient digital environments that protect against emerging cyber threats.
Frequently Asked Questions
What are the key components of a network?
Understanding a network involves recognising its key components, including physical infrastructure (like routers, switches, and cables), logical components (such as protocols and operating systems), and security management tools (like firewalls and monitoring software).
How does data travel through a network?
Data travels in packets via packet-switching techniques. Each packet is segmented and addressed for independent routing through the network, ensuring efficient and secure data transmission.
How can I secure my home network effectively?
To secure your home network, change your router’s default credentials, keep firmware updated, protect your SSID, use strong encryption protocols (like WPA3), and monitor connected devices regularly.
What is multipath data transmission and why is it important?
Multipath data transmission allows packets to travel through multiple routes simultaneously, enhancing data transfer speed, reducing latency, and providing redundancy to prevent complete transmission failures.
Strengthen Your Network Security with Re-Solution’s Expertise
In the face of growing digital threats, understanding your network is crucial for preserving your valuable data and ensuring smooth operations. If you’re concerned about the 62% of data breaches linked to compromised user credentials and seeking robust security measures, Re-Solution is here to help.
!
Our seasoned team, leveraging over 35 years of expertise as trusted Cisco partners, excels in crafting tailored network solutions that address your specific pain points:
- Managed IT Services to safeguard your infrastructure
- Network as a Service (NaaS) for flexible, scalable options
- Comprehensive Infrastructure Audits and Network Surveys highlighting vulnerabilities
- Custom Security and Compliance Solutions to keep your data secure
Don’t leave your network security to chance. Contact us today at https://re-solution.co.uk and let Re-Solution transform your network into a secure fortress, ensuring operational resilience and peace of mind for your business.
